UPDATED 12/4/24 12:45 AM ET
ORIGINALLY POSTED 12/4/24: 9:15 AM ET
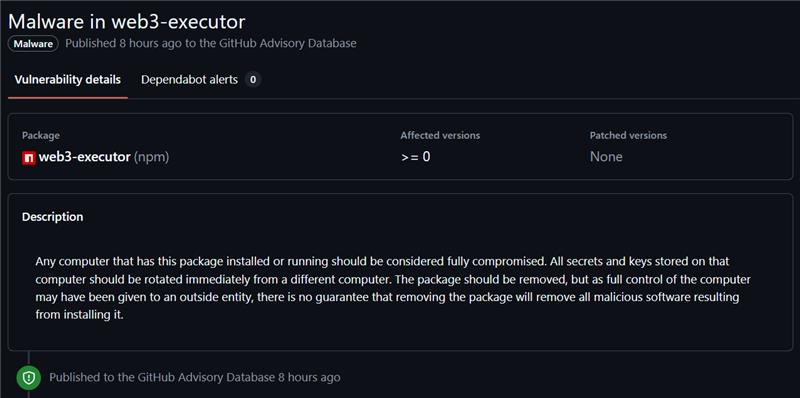
The Solana NPM package has been compromised.
GitHub have published a malware notice under their Advisory Database to inform users of this compromise. How long this package has been compromised for is still unknown, and current impact is still to be assessed. However, due to the popularity of this package it is likely that the impact will be high.
Treat any systems that use this package as fully compromised. All secrets, keys and sensitive information should be considered as such and rotated immediately.
According to security researcher Christophe Tafani-Dereeper on BlueSky: “The backdoor inserted in v1.95.7 adds an “addToQueue” function which exfiltrates the private key through seemingly-legitimate CloudFlare headers. Calls to this function are then inserted in various places that (legitimately) access the private key.”

Steven Luscher, one of the maintainers for the project said in the newest release notes “a publish-access account was compromised for @solana/web3.js, a JavaScript library that is commonly used by Solana dapps. This allowed an attacker to publish unauthorized and malicious packages that were modified, allowing them to steal private key material and drain funds from dapps, like bots, that handle private keys directly.” as the source of the compromise.
It is currently recommended to update to version 1.95.8 and rotate keys as a precautionary measure.
Source:
https://github.com/advisories/GHSA-fhm6-mqmw-2cf5
https://bsky.app/profile/did:plc:zwlpsxw2udovqf4mbfi4ibqf/post/3lcgt6l7s4c2a
https://github.com/solana-labs/solana-web3.js/releases/tag/v1.95.8

